Soft-Skill Attacks: How to Protect Against Social Engineering


Modern technologies are becoming more robust, and security measures more sophisticated. But there’s one vulnerability that can’t be patched — human trust. This is why cybercriminals increasingly target not just IT infrastructure but human behavior itself. They don’t need access to your code if they can get access to your people — by creating panic, urgency, or a well-crafted “official” request.
The problem is not a lack of knowledge, but human psychology. People tend to trust — especially when someone poses as tech support, an old colleague, or a manager. Many people are also prone to panic and time pressure (“urgent action needed”, “deal is falling through”, “account will be blocked”).
Sometimes just a few details are enough — an employee name, a contract number, a product name. Such information is easy to gather through OSINT (Open Source Intelligence): LinkedIn, tenders, press releases, corporate pages. Knowing a bit of context — staff names, order numbers, contract references, vendor names — allows fraudsters to appear legitimate, even without any access to internal systems. That’s all it takes to make an attack look believable.
Emails from a “bank”, notifications from a fake “payment system”, phone calls from a “security department” — all designed to impersonate a trusted source. A fake website, a domain typo, an alarming SMS (“$320 withdrawn from your card”) — and the victim calls back to “verify the details”.
Fraudsters insert themselves into legitimate business correspondence — by hacking an email or spoofing a domain that’s just one character different. They impersonate a CEO, lawyer, or colleague, sending a message demanding urgent payment. To appear credible, they may forward a forged email chain to look like prior approval, adding the target in the final thread. Everything looks routine — but the money goes to the fraudster.
Attackers enter offices posing as couriers, contractors, or new interns. Their goal: gain physical access to infrastructure, plug in a USB, connect to Wi-Fi, or photograph login details. These attacks are especially dangerous for companies with weak access controls.
Admins and support teams are a prime target — they have privileged access, system credentials, and admin rights. A single compromised login can give an attacker control over an entire network and employee accounts.
Experts project that global losses from cybercrime will reach $10.5 trillion by the end of 2025. Social engineering is not only still one of the top attack vectors — it’s becoming more scalable and more sophisticated.
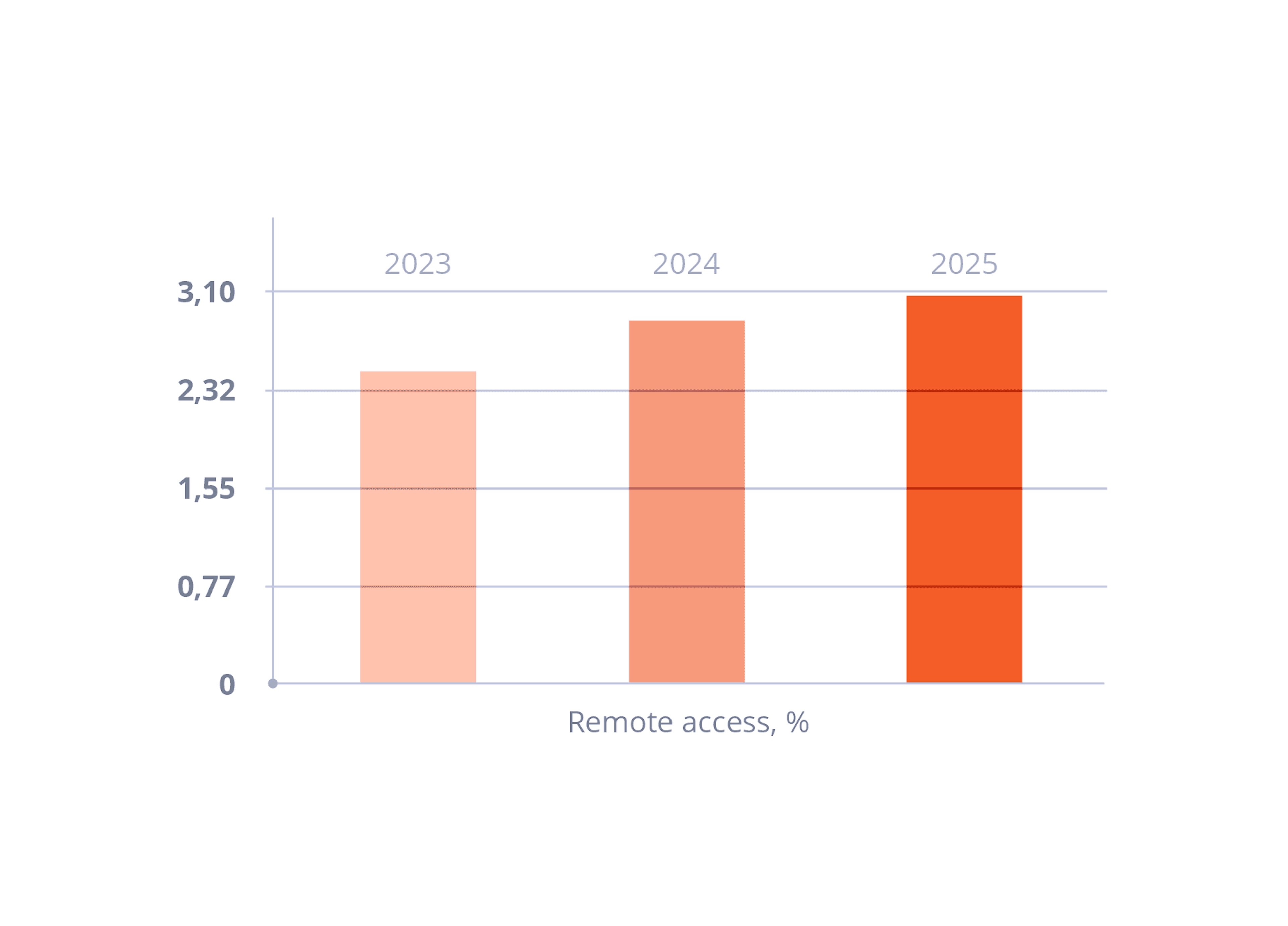
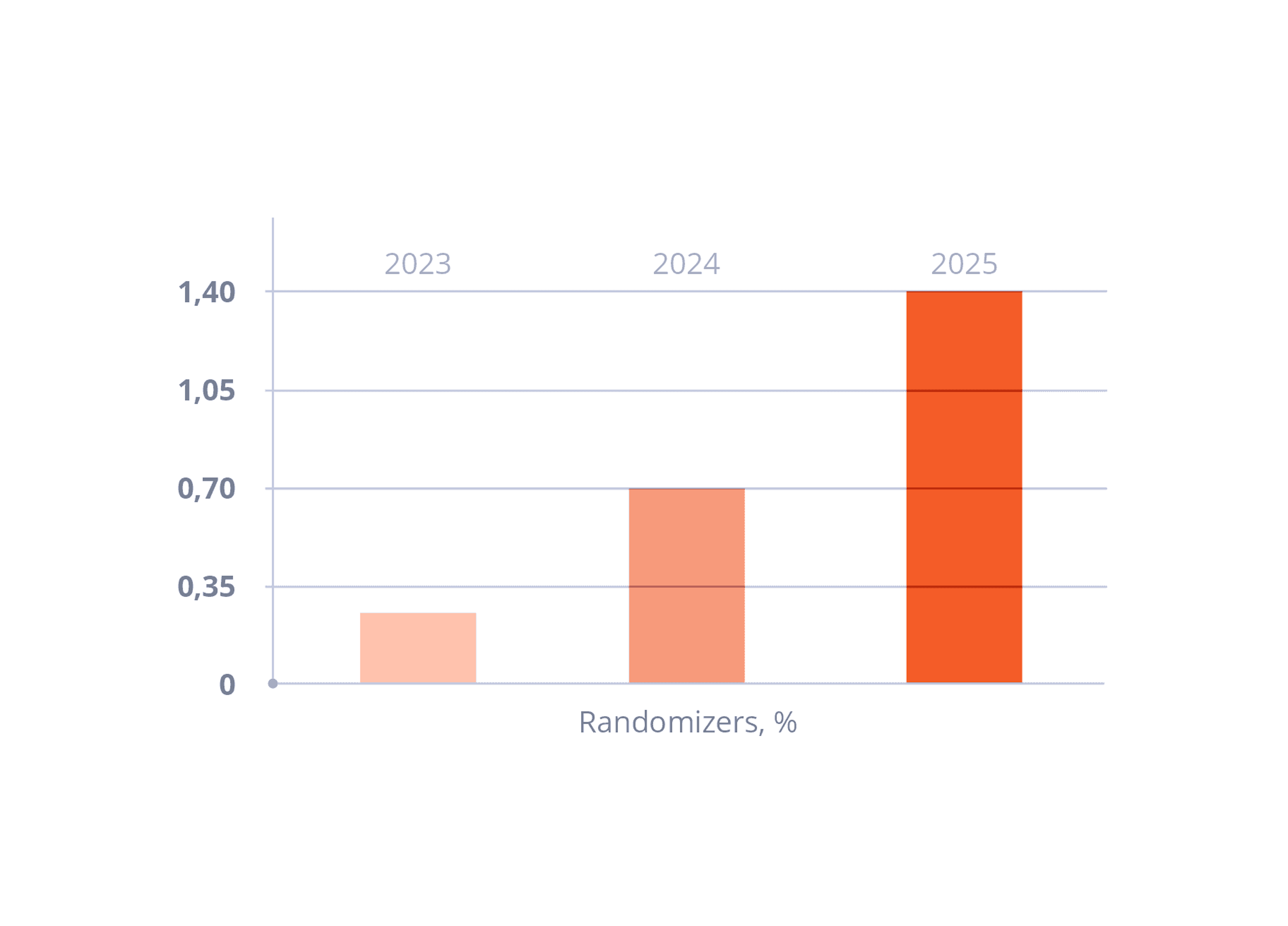
Statistics show that the share of incidents involving remote access and digital footprint obfuscation has grown significantly over the past two years — and continues to rise. What used to be rare is now the norm: by 2025, more attackers will use remote connections and randomization techniques to hide their traces. This means attacks increasingly combine social engineering with technical evasion — gaining access to corporate resources with stolen credentials and masking real activity.
Attackers gather intelligence from open sources: LinkedIn, company websites, press releases, social media posts. The goal is clear — map out the company’s structure, identify key people, clients, vendors and exploit that context for targeted fraud.
Social engineering relies on urgency and pressure tactics: “the deal will collapse”, “only 3 minutes left”:
Use real-life cases, attack simulations, and phishing drills. Make cyber risk awareness part of your company culture — not just a checkbox exercise.
Implement Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA), limit user permissions, and segment your network.
Check what information about your company is public: org charts, contacts, tech stacks. What seems harmless can be a weapon for attackers.
Social engineering is an attack on people, not systems. It doesn’t require malware or backdoors — just a convincing pretext and the right moment. No antivirus can protect against it if the user doesn’t know they’re being deceived. The best defense is not only automation but regular training, simulation exercises, and a strong security culture.
Today, advanced risk management and anti-fraud solutions can detect multiple technical signals that help identify suspicious scenarios:
Remote Access:
Obfuscation & Randomization:
Active Calls:
Behavioral Anomalies:
Credit Activity:
Connection Speed:
…and other metrics.
These and other indicators are available for integration to detect remote access and social engineering scenarios as part of robust fraud risk management.
We’re not standing still — we’re continuously expanding our technology stack. In our upcoming product releases, powered by API17, we plan to significantly enhance our capabilities for detecting social engineering patterns and related threats.

Modern web applications use dynamic interfaces based on the DOM (Document Object Model).

API 16: +50 IV% and +25% Gini — Your Key to Business Safety
An expert article by JuicyScore's Business Development Manager, featuring first-hand insights on fintech expansion in Latin America. Discover how digital signals and device intelligence are redefining risk assessment in high-fraud environments.
Get a live session with our specialist who will show how your business can detect fraud attempts in real time.
Learn how unique device fingerprints help you link returning users and separate real customers from fraudsters.
Get insights into the main fraud tactics targeting your market — and see how to block them.
Phone:+971 50 371 9151
Email:sales@juicyscore.ai
Our dedicated experts will reach out to you promptly