JuicyID v16: Enhanced Protection Against Secondary Fraud


Research shows that multi-accounting increases fraud risks by 30–60%, while financial institutions' losses from secondary fraud can reach 15–20% of the credit portfolio turnover. Even managing already verified clients after the initial application leads to significant operational losses. Despite lower fraud rates among such clients, the volume of returning customers can generate losses exceeding those from new customers.
In the latest version of JuicyID, we have made significant changes to 15 variables and introduced 20 new ones, enhancing protection not only for personal accounts and mobile applications but also for preventing credit shopping and multi-accounting among verified clients. These risks, along with remote access and social engineering, account for the majority of losses among repeat customers.
JuicyID now analyzes not only primary behavioral anomalies but also secondary signals, such as attempts to bypass restrictions, advanced signs of rooting, and remote access. This enables early detection of repeated fraud attempts.
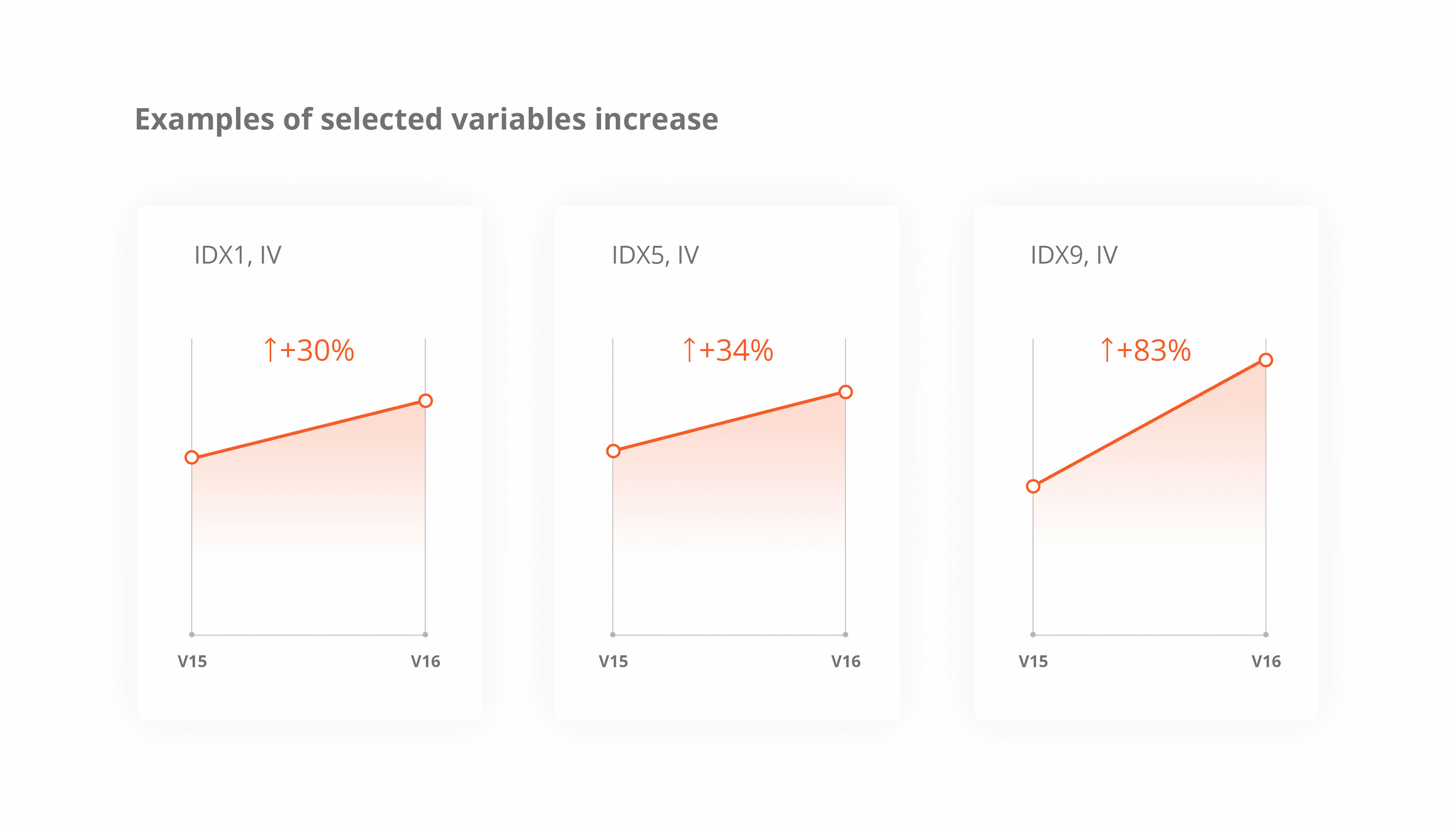
The updated IDX1, IDX5, and IDX9 indices allow for a deeper analysis of fraud risks by assessing behavioral anomalies and fraud likelihood at different stages of the credit cycle.
IDX1 – Identifies primary fraud risks by analyzing key anomalies. Its effectiveness depends on the credit cycle stage where it is applied—whether for initial screening or during repeat applications.
IDX5 – Assesses device quality, detecting signs of reliability or potential fraud. It helps determine whether a device is stable and aligns with normal user behavior.
IDX9 – Analyzes software and device-related risks, including proxy detection, use of high-risk applications (gambling, micro-lending, unofficial services), and suspicious actions such as factory resets, frequent reboots, and other fraud indicators.
Filtering fraudsters at the entry point is only the first step. They may return, test the system, and look for vulnerabilities. Common fraud scenarios observed across different regions:
These scenarios confirm that previously approved clients require additional verification.
JuicyID helps detect recurring fraud patterns, track behavioral trends, and identify fraud at later stages, where traditional methods are no longer effective.
The enhanced JuicyID is already being used in multiple countries, helping to uncover hidden risks and strengthen financial platform security.
The product delivers real results: it not only effectively blocks fraudsters at the entry point but also prevents repeat attacks—critical for fintech, marketplaces, and classifieds.
For example, in eight years of successful collaboration with a leading anti-fraud solutions provider, a top international fintech group implemented JuicyID to reduce risks in repeat lending. The new technology enabled the detection of additional risk markers, including unusual language usage, virtual machines, and non-standard devices. As a result, the company reduced early-stage repeat loan risks by several percentage points, demonstrating JuicyID’s effectiveness in combating secondary fraud.
One study on JuicyID’s applicability revealed a 30%+ reduction in overall losses among verified clients.
Analysis showed that traditional security measures, such as 2FA+ and standard risk assessment procedures, are insufficient to fully neutralize fraudulent schemes. The key loss structure highlighted:
Based on the study, additional protection measures were proposed:
JuicyID continues to evolve, offering fintech companies and banks a new level of fraud protection. Its innovative approach—based on hidden digital marker analysis and behavioral insights—not only effectively detects fraudsters at the entry stage but also prevents complex secondary fraud schemes. By combining deep analytics, alternative data processing, and adaptive algorithms, JuicyID provides a powerful tool against digital threats, helping companies optimize risk models, minimize losses, and enhance resilience against fraud attacks.
An expert article by JuicyScore's Business Development Manager, featuring first-hand insights on fintech expansion in Latin America. Discover how digital signals and device intelligence are redefining risk assessment in high-fraud environments.

API 16: +50 IV% and +25% Gini — Your Key to Business Safety

Modern web applications use dynamic interfaces based on the DOM (Document Object Model).
Get a live session with our specialist who will show how your business can detect fraud attempts in real time.
Learn how unique device fingerprints help you link returning users and separate real customers from fraudsters.
Get insights into the main fraud tactics targeting your market — and see how to block them.
Phone:+971 50 371 9151
Email:sales@juicyscore.ai
Our dedicated experts will reach out to you promptly