JuicyFilter: a solution for commercial and lead generation fraud prevention


Modern online companies need not only to find new channels to attract customers and sell their services in the market but also to be able to analyze the quality of these channels and assess the associated risks.
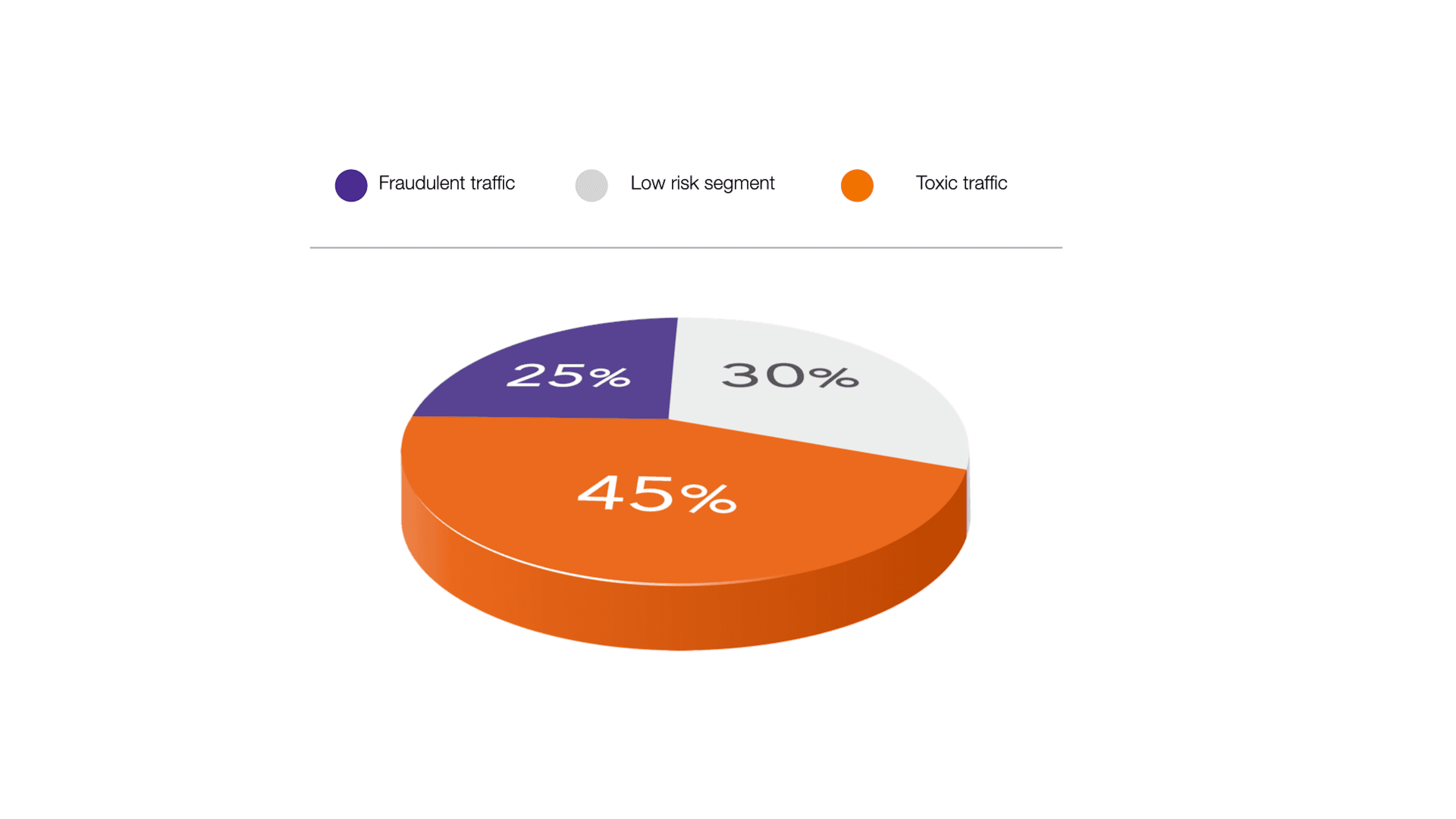
One of the main problems of fraud in the commercial environment is that the barrier to entry is lower than in credit risks, and accordingly, the level of fraud is higher. It results in the fact that the entry barrier for online fraudsters is significantly lower. They do not need to search for data or vulnerabilities in the market of personal data sources. As our estimates show, on average, 25-30% of traffic is either artificial or toxic. Meanwhile, the industry sees the highest level of fraudsters.
Another problem is the inability of professional lead generators to clearly identify the source of either high-quality or poor traffic. Despite the fraud itself (potentially risky traffic), companies also face low-quality toxic traffic, which practically does not convert and can exceed the size of the fraud. Following our expertise, all traffic can be divided into several major groups:
All available methods of attracting traffic online can be divided into two major groups. They involve independent traffic generation (known as organic traffic) and utilizing partner resources (affiliate or partnership marketing campaigns).
Organic traffic fraud is often associated with the generation of "non-productive" traffic. Studies show that humans generate less than 60-70% of internet traffic. Ad fraud significantly impacts campaign effectiveness and ROI, despite the promotion budget.
Cheating competitors may use click fraud to distort an online company's organic traffic assessment. It can be achieved through displayed ads, videos, social media channels, or searches, often using anonymous VPNs. Such traffic does not generate revenue, which may prompt companies to abandon this promotion channel. Click bots, programs for automatic ad clicking, are becoming increasingly popular. They account for 20 to 60% of all clicks, negatively impacting return on investment.
Bots are automated software applications that visit websites or use online services. However, it is worth noting that not all bots are harmful. For instance, search engine scanners, that index web pages, help improve search results. On the other hand, malicious bots collect data or initiate DDoS attacks. Companies need to recognize bot traffic to secure their resources and ensure the reliability of their online operations.
Malicious bots can distort website analytics, leading to inaccurate data analysis and unverified business decisions. They can consume server resources and telecommunication channels, slow down website performance, or cause downtime, resulting in losses. Scraping bots can steal content, thereby violating intellectual property rights and damaging brand reputation. Additionally, setting up bot blocking and detection can strengthen a business's network and server infrastructure against DDoS attacks and hacking attempts.
SDK-Spoofing is a relatively new type of mobile fraud that involves creating the appearance of mobile app installations using malicious code at the SDK file level. Click injection in some way is similar to fraud using click bots when it comes to affiliate marketing fraud. When the Android app is being installed, device-related malicious software initiates a click on the app, attributed to its advertising account. Thus, for each click, the company pays money to the affiliate who did not actually bring the customer to the target page.
Cookie stuffing is one of the most common types of fraud associated with affiliate marketing. A fraudster can discreetly add dozens of affiliate resources to a company's website by replacing the browser's cookie files. When a user clicks on a link and performs a targeted action, the company pays a commission for a lead that it essentially generated itself. This fraudulent scheme also results in traffic that initially has no conversion potential.
The main red flags of this type of fraud may include a sudden increase in expenses for affiliate marketing without a proportionate or noticeable increase in ROI.
Ad stacking is a common type of mobile fraud. It mainly occurs in advertising with payments per click. Here, multiple ads are stacked on top of each other letting the user see only the top one. As a result, the advertiser pays for impressions and clicks, even though the user doesn't see the ads.
Pixel stuffing considers placing ads in a confined website area, for example, as small as 1 by 1 pixel. The user doesn't see this advertisement, but the company is still charged for impressions.
Businesses need a solution to keep their 1 USD-worth assets safe. To make it possible, we have developed a new solution called JuicyFilter. It is a reliable safety mean for downloading applications, media assets, and basic bot filtering. Currently, we are in the final stages of developing the new product.
Essentially, JuicyFilter is a system that reacts to signals, which is involved in the decision-making process. In case of risk, the system triggers back-push events. This solution will address a range of tasks:
The JuicyFilter solution makes it possible to significantly filter out apps with signs of high risk. It also detects globally soaring commercial fraud. We provide one of the fastest and most effective solutions on the market (response occurs with a delay of 200-300 milliseconds, including data delivery time), and we are very pleased that our solution can exceed our clients’ expectations.
JuicyScore experts recommend that companies operating online adapt their anti-fraud technologies to keep up with the constantly evolving methods of online fraud and counter new types of commercial fraud. Utilizing alternative assessment tools on their platforms will provide a significant competitive advantage to brokers and aggregators.
Get a live session with our specialist who will show how your business can detect fraud attempts in real time.
Learn how unique device fingerprints help you link returning users and separate real customers from fraudsters.
Get insights into the main fraud tactics targeting your market — and see how to block them.
Phone:+971 50 371 9151
Email:sales@juicyscore.ai
Our dedicated experts will reach out to you promptly