Virtual Machine Detection: The Overlooked Risk Factor in Digital Lending

In a world where digital services dominate the financial landscape, fraud is increasingly found within sophisticated, hard-to-detect layers of technology. It disguises itself in complex technical environments – among them, virtual machines (VMs). While these tools serve legitimate purposes in IT infrastructure and cybersecurity, they are also being used by bad actors to obscure identity, emulate devices, and bypass verification systems.
For decision-makers in digital lending, banking, microfinance, BNPL, and fintech, virtual machine detection is becoming a cornerstone capability in any effective risk management stack.
A virtual machine (VM) is a software-based emulation of a physical computing environment. It functions like a traditional device – running operating systems, executing programs, and accessing the internet – but it doesn’t physically exist. Instead, it operates as a guest within a host system, relying on virtualization software such as VMware, VirtualBox, or Hyper-V.
From the perspective of most applications and systems, a VM behaves like a standard desktop, laptop, or smartphone. That’s exactly what makes it useful – and risky.
In enterprise IT, VMs are indispensable. They support scalability, optimize hardware usage, and enable developers to test code in isolated environments. In cybersecurity, they provide sandbox environments to safely analyze malware. In DevOps, they enable rapid deployment and rollback across production systems.
However, in the context of digital lending, banking, or any high-value transactional environment, VMs take on a different character.
Because they can mimic clean, new devices and reset identity markers between sessions, virtual machines are often exploited to commit fraud and are frequently used in three high-risk scenarios:
To understand the distinction between virtual machines and real devices, consider the following technical characteristics:
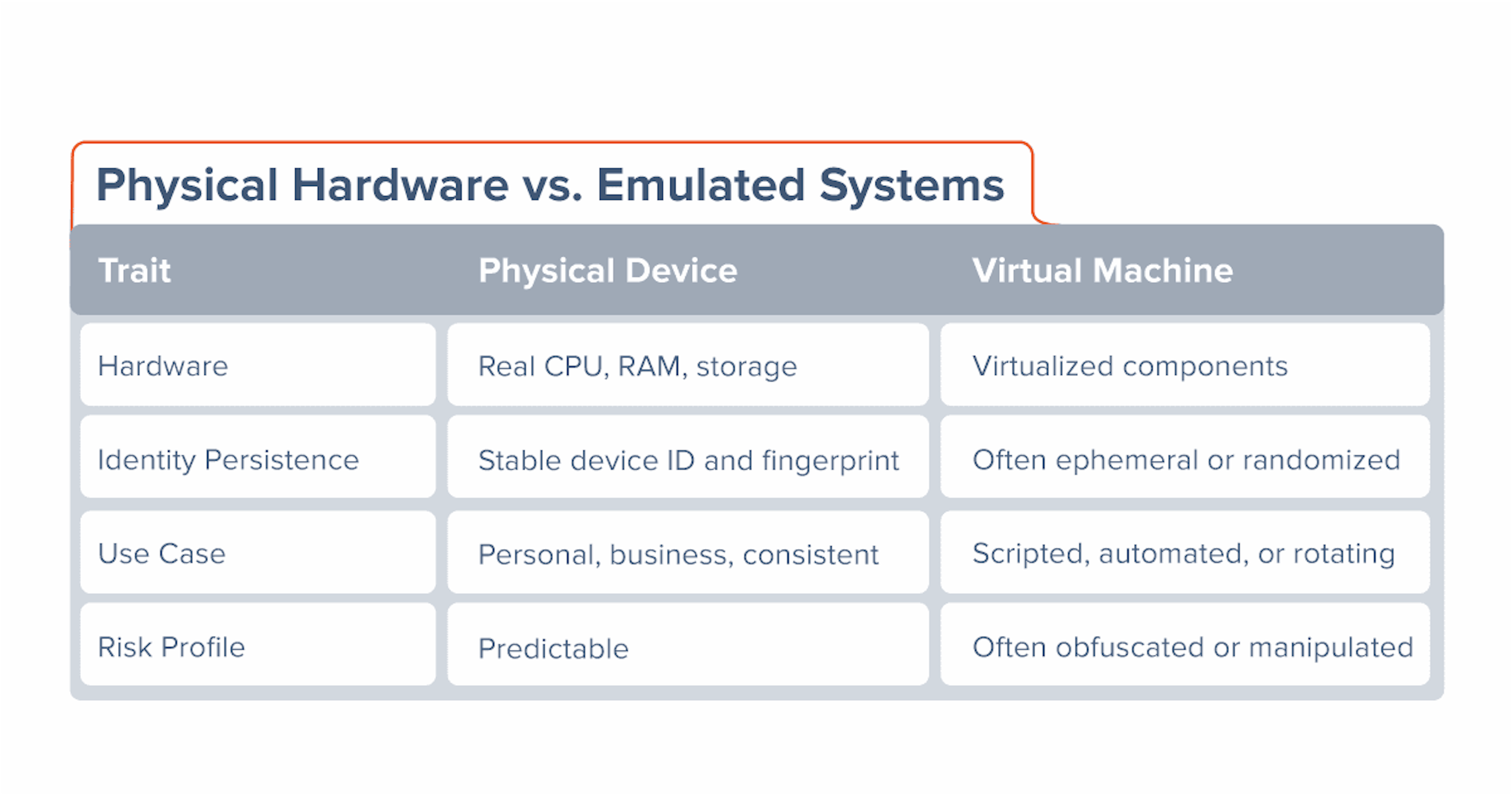
This environment’s ability to mask true device characteristics is what makes it risky. Fraud prevention systems often rely on attributes like device ID, session history, or behavioral norms – all of which can be masked, spoofed, or rotated in a virtualized environment.
Not all VMs are equally risky. We can classify them into three general categories:
Though detecting VMs can be challenging, some common indicators include:
These signs become even more useful when combined with behavioral data – such as scrolling patterns, input velocity, or session replay irregularities – helping separate genuine users from automated fraud flows.
JuicyScore's research on the risk of virtual machines shows that:
In other words, detecting VMs isn't just a technical concern – it's directly tied to portfolio quality and business performance.
Virtual machine detection works by identifying the subtle yet consistent technical and behavioral discrepancies that distinguish virtualized environments from genuine, physical devices. While virtual machines are often used for legitimate purposes such as testing or development, in the context of financial services and online lending, their presence can signal heightened risk. Fraud actors commonly use VMs to simulate user behavior at scale, mask their identity, or bypass rule-based controls – creating the illusion of legitimacy while launching automated attacks or repeated application attempts.
JuicyScore’s approach to virtual machine detection relies on a multi-dimensional analysis of both device integrity and session behavior. Rather than looking for a single red flag, our methodology aggregates dozens of technical signals – such as rendering anomalies, browser inconsistencies, performance benchmarks, and signs of fingerprint obfuscation – to classify devices across a four-tier risk framework: physical, virtual, randomized physical, and randomized virtual.
These insights are translated into proprietary index variables (like IDX1 and IDX3), which power real-time, probabilistic scoring decisions.
This allows our clients to identify emulated environments with high confidence – filtering out high-risk traffic before onboarding, authentication, or transaction approval occurs, all without compromising privacy.
Book a free JuicyScore demo today to see how real-time virtual machine detection can protect your business, increase scoring accuracy, and strengthen your compliance strategy.
Virtual machine detection is the process of figuring out whether a user is interacting with your platform from a real physical device or a software-based virtual environment. In fintech, that distinction matters because virtual machines are often used to hide identity, bypass device checks, or automate fraud at scale.
No – many are legitimate. Virtual machines are a normal part of corporate IT – used for things like software testing, secure environments, and DevOps workflows. However, when they show up in lending applications, onboarding flows, or transactional sessions, especially with other signs of manipulation, they can indicate high-risk behavior.
It’s not just one signal. Detection relies on a combination of factors: subtle rendering inconsistencies, mismatched hardware specs, missing mobile sensors, behavioral anomalies like uniform mouse movement, and more.
VMs give fraud actors flexibility. They can quickly spin up new environments, erase traces between sessions, bypass device bans, and even run automated scripts to submit fake applications. In short, they can look like a new user every time – unless you’re actively checking for virtualization.
Yes – and the data confirms it. JuicyScore’s data shows that applications flagged as virtualized environments have up to 3x higher default risk. By detecting and filtering them early in the decision flow, lenders can significantly reduce chargebacks, defaults, and the cost of manual reviews – leading to better risk outcomes across the board.
What is device fingerprinting and why is it crucial in fraud prevention?
Learn how to prevent bot attacks and protect your business from fraud.

What is application fraud, how does it work, and how to prevent it?
Get a live session with our specialist who will show how your business can detect fraud attempts in real time.
Learn how unique device fingerprints help you link returning users and separate real customers from fraudsters.
Get insights into the main fraud tactics targeting your market — and see how to block them.
Phone:+971 50 371 9151
Email:sales@juicyscore.ai
Our dedicated experts will reach out to you promptly